CKS考试真题
1、kube-bench 修复不安全项
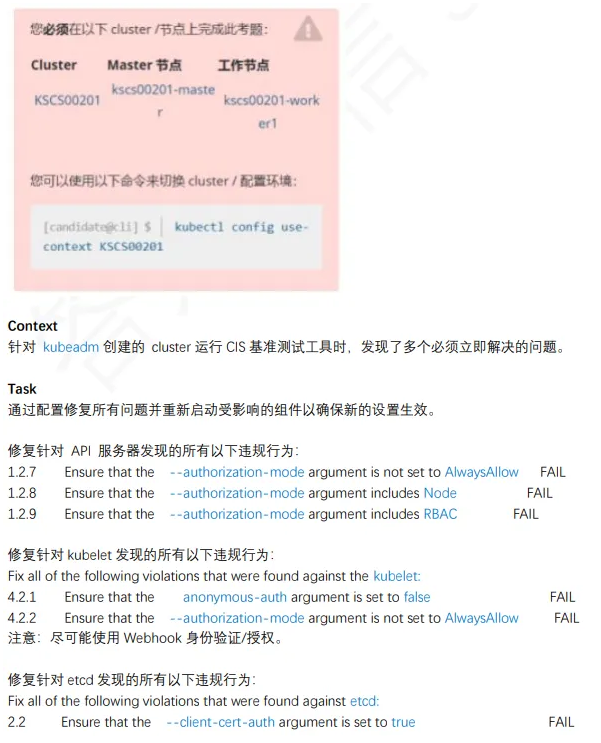
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| linux@node1:~$ kubectl config use-context k8s
重启⼀下服务
linux@node1:~$ ssh master
linux@master:~$ sudo -i
root@master01:~$ cp /etc/kubernetes/manifests/kube-apiserver.yaml /tmp
root@master01:~$ cp /etc/kubernetes/manifests/etcd.yaml /tmp
root@master01:~$ cp /var/lib/kubelet/config.yaml /tmp
root@master:~$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
- --authorization-mode=Node,RBAC
- --insecure-bind-address=0.0.0.0
root@master:~$ vim /var/lib/kubelet/config.yaml
anonymous:
enabled: false
webhook:
enabled: true
authorization:
mode: Webhook
root@master:~$ vim /etc/kubernetes/manifests/etcd.yaml
- --client-cert-auth=true
root@master:~$ systemctl daemon-reload
root@master:~$ systemctl restart kubelet
root@master01:~$ kubectl get pod -A
exit,exit
|
参考链接:https://kubernetes.io/zh-cn/docs/reference/config-api/kubelet-config.v1beta1/
2、Pod 指定ServiceAccount
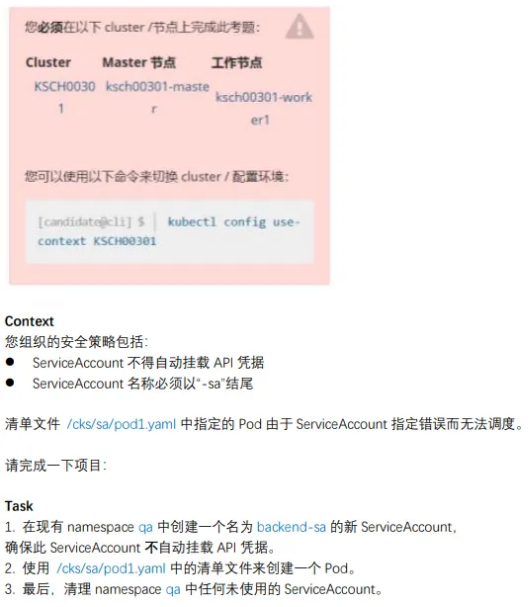
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| linux@node1:~$ kubectl config use-context KSCH00301
linux@node1:~$ vim qa-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: backend-sa
namespace: qa
automountServiceAccountToken: false
linux@node1:~$ kubectl apply -f qa-sa.yaml
serviceaccount/abckend-sa created
linux@node1:~$ kubectl get sa -n qa
NAME SECRETS AGE
abckend-sa 0 10s
default 0 24d
test01 0 24d
linux@node1:~$ vim /cks/sa/pod1.yaml
apiVersion: v1
kind: Pod
metadata:
name: backend
namespace: qa
spec:
serviceAccountName: backend-sa
认已有这⼀⾏,需要修改。)
containers:
- image: nginx:1.9
imagePullPolicy: IfNotPresent
name: backend
linux@node1:~$ kubectl apply -f /cks/sa/pod1.yaml
linux@node1:~$ kubectl get pods -n qa
NAME READY STATUS RESTARTS AGE
backend 1/1 Running 0 117s
qatt 1/1 Running 3 (46m ago) 24d
linux@node1:~$ kubectl get sa -n qa
linux@node1:~$ kubectl get pods -n qa -o yaml | grep -i ServiceAccountName
linux@node1:~$ kubectl delete sa test01 -n qa
|
参考链接:https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/
3、默认网络策略
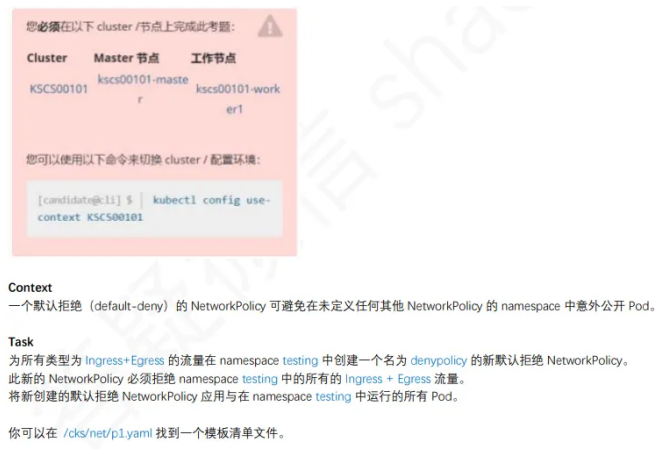
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| linux@node1:~$ kubectl config use-context KSCS00101
linux@node1:~$ vim /cks/net/p1.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: denypolicy
namespace: testing
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
linux@node1:~$ kubectl apply -f /cks/net/p1.yaml
linux@node1:~$ kubectl describe networkpolicy denypolicy -n testing
|
参考链接:https://kubernetes.io/docs/concepts/services-networking/network-policies/
4、RBAC - RoleBinding
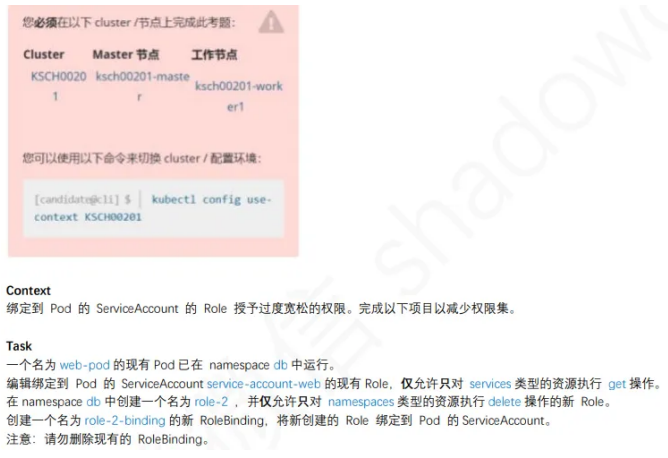
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| linux@node1:~$ kubectl config use-context KSCH00201
linux@node1:~$ kubectl describe rolebinding -n db
linux@node1:~$ kubectl edit role role-1 -n db
……
rules:
- apiGroups: [""]
resources: ["services"]
verbs: ["get"]
linux@node1:~$ kubectl create role role-2 --verb=delete --resource=namesp
aces -n db
linux@node1:~$ kubectl create rolebinding role-2-binding --role=role-2 --
serviceaccount=db:service-account-web -n db
linux@node1:~$ kubectl describe rolebinding -n db
|
参考链接:https://kubernetes.io/docs/reference/access-authn-authz/rbac/#role-and-clusterrole
5、⽇志审计 log audit
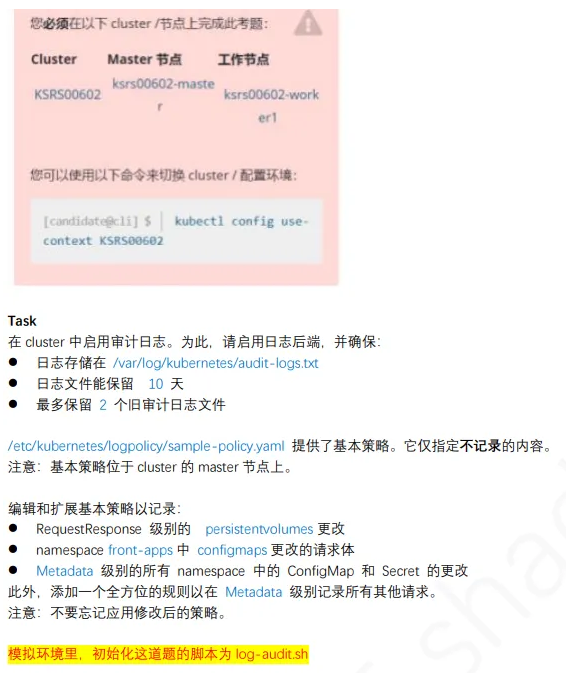
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| linux@node1:~$ kubectl config use-context KSH
1、切换环境
linux@node1:~$ ssh master
linux@master:~$ sudo -i
root@master:~$ cp /etc/kubernetes/logpolicy/sample-policy.yaml /tmp
root@master:~$ cp /etc/kubernetes/manifests/kube-apiserver.yaml /tmp
root@master:~$ vim /etc/kubernetes/logpolicy/sample-policy.yaml
- level: RequestResponse
resources:
- group: ""
resources: ["persistentvolumes"]
- level: Request
resources:
- group: ""
resources: ["configmaps"]
namespaces: ["front-apps"]
- level: Metadata
resources:
- group: ""
resources: ["secrets", "configmaps"]
- level: Metadata
omitStages:
- "RequestReceived"
root@master:~$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
- --audit-policy-file=/etc/kubernetes/logpolicy/sample-policy.yaml
- --audit-log-path=/var/log/kubernetes/audit-logs.txt
- --audit-log-maxage=10
- --audit-log-maxbackup=2
root@master:~$ systemctl daemon-reload
root@master:~$ systemctl restart kubelet
root@master:~$ kubectl get pods -A
root@master:~$ tail /var/log/kubernetes/audit-logs.txt
exit
exit
|
参考链接:https://kubernetes.io/docs/tasks/debug/debug-cluster/audit/#audit-policy
6、创建Secret
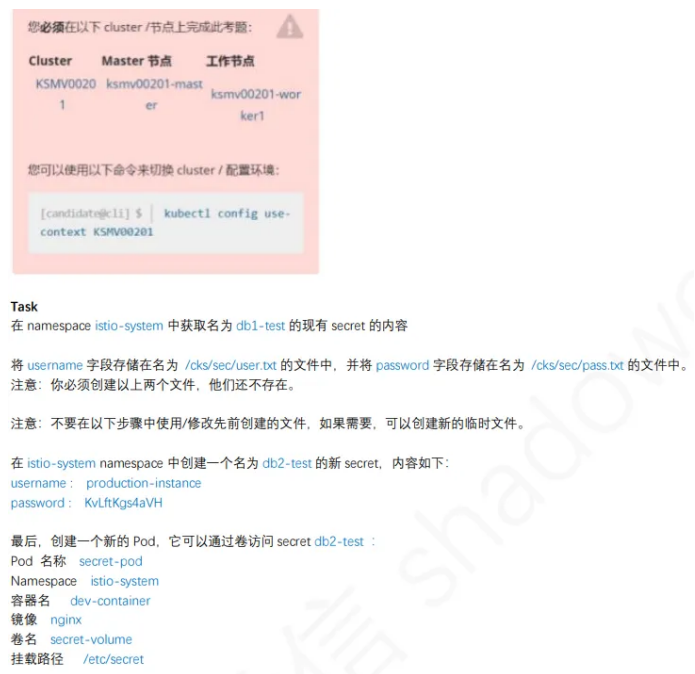
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
linux@node1:~$ kubectl get secrets db1-test -n istio-system -o yaml
linux@node1:~$ echo 'ZGIx' | base64 -d > /cks/sec/user.txt
linux@node1:~$ echo 'aGVsbG8=' | base64 -d > /cks/sec/pass.txt
linux@node1:~$ cat /cks/sec/user.txt
db1linux@node1:~$ cat /cks/sec/pass.txt
hellolinux@node1:~$
linux@node1:~$ kubectl create secret generic db2-test -n istio-system
--from-literal=username=production-instance --from-literal=password=KvLftKgs4aVH
linux@node1:~$ kubectl get secret -n istio-system
NAME TYPE DATA AGE
db1-test Opaque 2 24d
db2-test Opaque 2 42s
linux@node1:~$ vim k8s-secret.yaml
apiVersion: v1
kind: Pod
metadata:
name: secret-pod
namespace: istio-system
spec:
containers:
- name: dev-container
image: nginx
volumeMounts:
- name: secret-volume
mountPath: "/etc/secret"
volumes:
- name: secret-volume
secret:
secretName: db2-test
linux@node1:~$ kubectl apply -f k8s-secret.yaml
pod/secret-pod created
linux@node1:~$ kubectl get pod -n istio-system
NAME READY STATUS RESTARTS AGE
secret-pod 1/1 Running 0 21s
|
参考链接:https://kubernetes.io/zh-cn/docs/concepts/configuration/secret/
7、Dockerfile检测
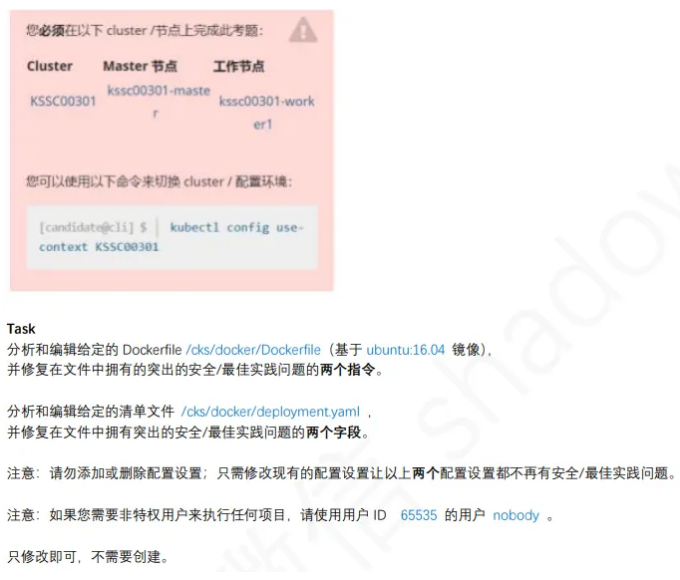
1
2
3
4
5
6
7
8
9
10
11
12
13
| linux@node1:~$ kubectl config use-context KSSC
linux@node1:~$ vim /cks/docker/Dockerfile
FROM ubuntu:22.04
USER nobody
linux@node1:~$ vim /cks/docker/deployment.yaml
app: couchdb
securityContext:
{'capabilities': {'add': ['NET_BIND_SERVICE'], 'drop': ['all']}, 'privileged': False, 'readOnlyRootFilesystem': True, 'runAsUser': 65535}
|
参考链接:https://kubernetes.io/docs/concepts/security/pod-security-standards/
8、沙箱运⾏容器gVisor
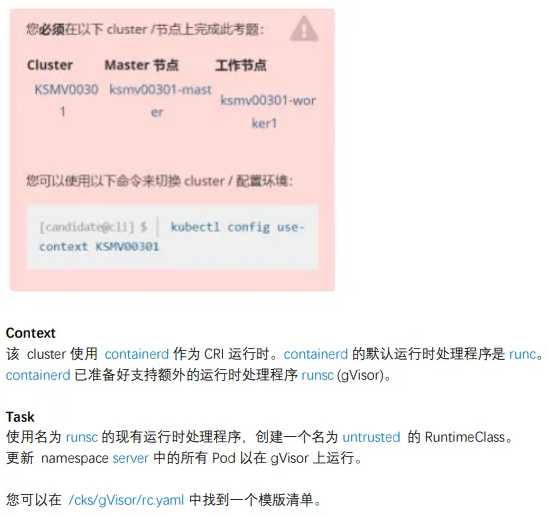
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| linux@node1:~$ kubectl config use-context KSMV
1 、创建RuntimeClass
linux@node1:~$ vim /cks/gVisor/rc.yaml
apiVersion: node1.k8s.io/v1
kind: RuntimeClass
metadata:
name: untrusted
handler: runsc
linux@node1:~$ kubectl apply -f /cks/gVisor/rc.yaml
linux@node1:~$ kubectl get RuntimeClass
NAME HANDLER AGE
untrusted runsc 4m32s
linux@node1:~$ kubectl get deploy -n server
NAME READY UP-TO-DATE AVAILABLE AGE
busybox-run 1/1 1 1 26d
nginx-host 1/1 1 1 26d
run-test 1/1 1 1 26d
linux@node1:~$ kubectl edit deploy busybox-run -n server
linux@node1:~$ kubectl edit deploy nginx-host -n server
linux@node1:~$ kubectl edit deploy run-test -n server
spec:
runtimeClassName: untrusted
containers:
linux@node1:~$ kubectl get deploy -n server -o yaml | grep runtime
|
参考链接:https://kubernetes.io/docs/concepts/containers/runtime-class/
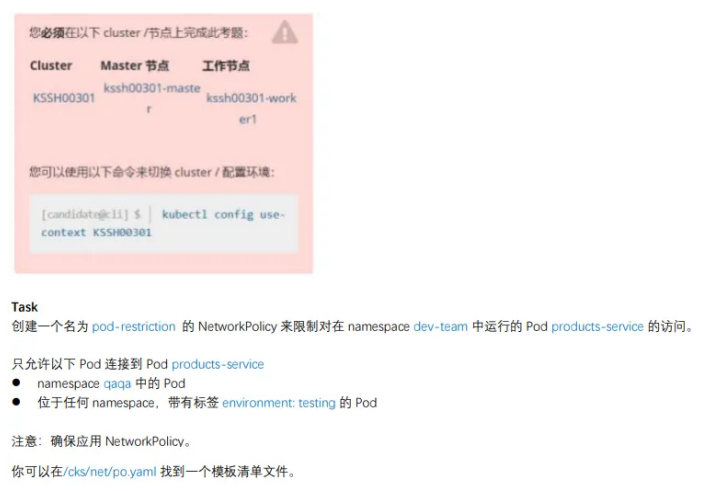
9、⽹络策略NetworkPolicy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| linux@node1:~$ kubectl config use-context KSS
linux@node1:~$ kubectl get ns --show-labels
linux@node1:~$ kubectl get pods -n dev-team --show-labels
NAME READY STATUS RESTARTS AGE LABELS
products-service 1/1 Running 3 (17h ago) 26d environment=testing
linux@node1:~$ vim /cks/net/po.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: pod-restriction
namespace: dev-team
spec:
podSelector:
matchLabels:
environment: testing
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
name: qaqa
- from:
- namespaceSelector: {}
podSelector:
matchLabels:
environment: testing
linux@node1:~$ kubectl apply -f /cks/net/po.yaml
linux@node1:~$ kubectl get networkpolicy -n dev-team
NAME POD-SELECTOR AGE
pod-restriction environment=testing 2m42s
|
参考链接:https://kubernetes.io/docs/concepts/services-networking/network-policies/
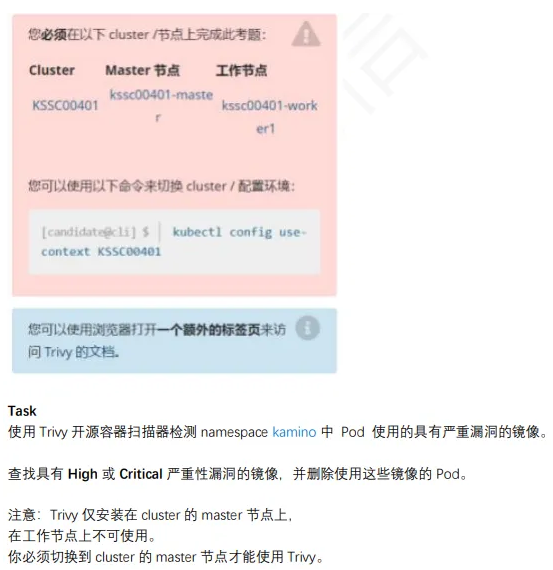
10、Trivy 扫描镜像安全漏洞
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
linux@node1:~$ kubectl config use-context KK
linux@node1:~$ ssh master
linux@master:~$ kubectl get pod -n kamino --output=custom-column
s="NAME:.metadata.name,IMAGE:.spec.containers[*].image"
NAME IMAGE
tri111 amazonlinux:1
tri222 amazonlinux:2,nginx:1.19
tri333 vicuu/nginx:host,amazonlinux:2
tri444 amazonlinux:2
linux@master:~$ for i in {amazonlinux:1,amazonlinux:2,nginx:1.19,vicuu/nginx:host}; do trivy image -s "HIGH,CRITICAL" $i >> 10.txt;done
linux@master:~$ cat 10.txt |grep -iB3 total
linux@master:~$ kubectl delete pod -n kamino tri222
|
参考链接:https://kubernetes.io/docs/reference/kubectl/quick-reference/
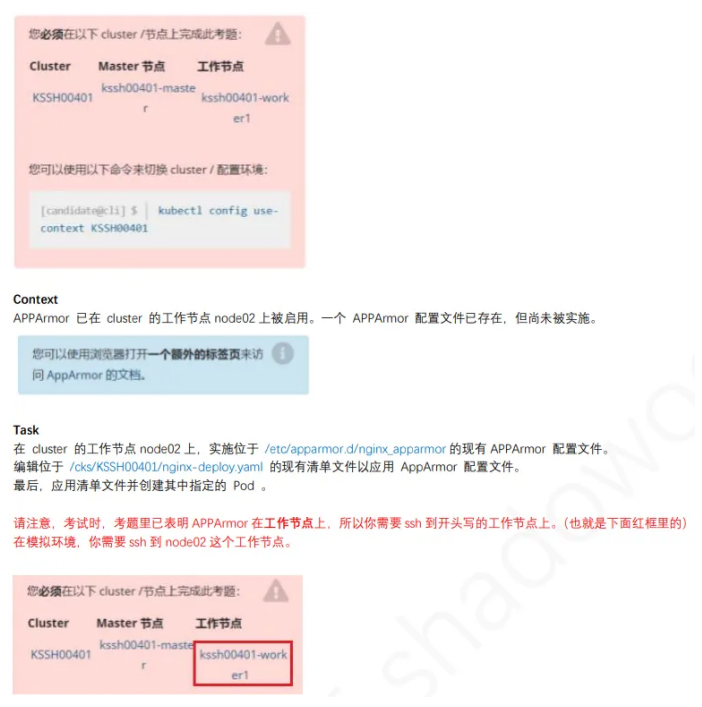
11、AppArmor
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
linux@node1:~$ kubectl config use-context KSSH
linux@node1:~$ ssh node2
linux@node2:~$ sudo -i
1、切换到/etc/apparmor.d/下启⽤apparmor
root@node2:~$ cd /etc/apparmor.d/
root@node2:/etc/apparmor.d$ cat nginx_apparmor
profile nginx-profile-3 flags=(attach_disconnected) {
个配置⽂件的名字
file,
deny /** w,
}
root@node2:/etc/apparmor.d$ apparmor_parser /etc/apparmor.d/nginx_apparmor
root@node2:/etc/apparmor.d$ apparmor_status | grep nginx-profile-3
root@node2:/etc/apparmor.d$ exit
linux@node2:~$ exit
linux@node1:~$ vim /cks/KSSH00401/nginx-deploy.yaml
annotations:
container.apparmor.security.beta.kubernetes.io/podx: localhost/nginx-profile-3
linux@node1:~$ kubectl apply -f /cks/KSSH00401/nginx-deploy.yaml
pod/podx created
linux@node1:~$ kubectl get pod
NAME READY STATUS RESTARTS AGE
podx 1/1 Running 0 99s
redis123-56c7cd579-wzk9f 1/1 Running 3 (38m ago) 26d
3、检查
linux@node1:~$ kubectl exec podx -- cat /proc/1/attr/current
nginx-profile-3 (enforce)
|
参考链接:https://kubernetes.io/zh-cn/docs/tutorials/security/apparmor/
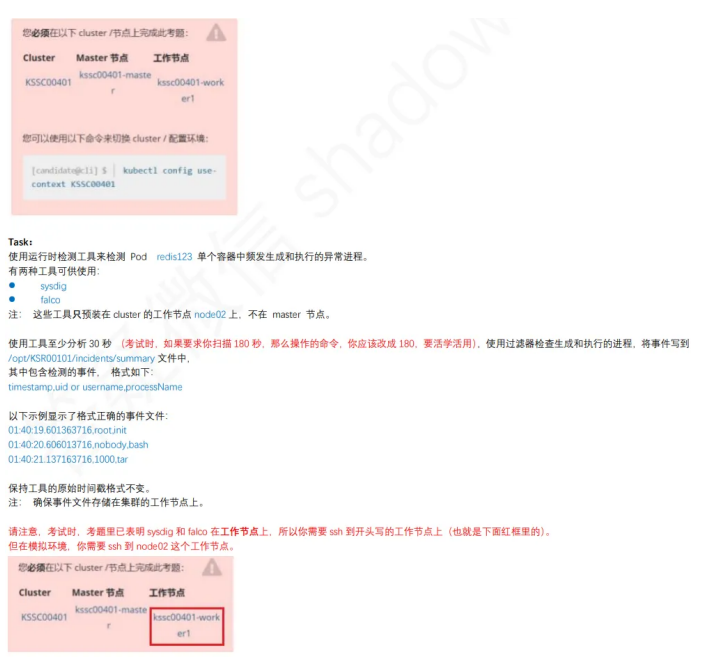
1 2 、 S y s d i g & f alc o
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
linux@node1:~$ kubectl config use-context KSSC00401
linux@node1:~$ ssh node2
linux@node2:~$ sudo -i
root@node2:~$ crictl ps | grep redis123
root@node2:~$ crictl info | grep sock
"containerdEndpoint": "/run/containerd/containerd.sock",
root@node2:~$ sysdig -M 30 -p "%evt.time,%user.name,%proc.name" --cri /ru
n/containerd/containerd.sock container.name=redis123 >> /opt/KSR00101/inci
dents/summary
root@node2:~$ sysdig -M 30 -p "%evt.time,%user.uid,%proc.name" --cri /run/
containerd/containerd.sock container.name=redis123 >> /opt/KSR00101/incidents/summary
root@node2:~$ cat /opt/KSR00101/incidents/summary
exit
exit
|
13、Container安全上下文
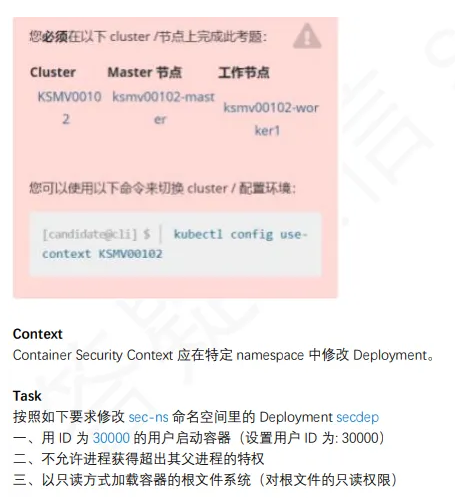
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
linux@node1:~$ kubectl config use-context KSMV
linux@node1:~$ kubectl edit deploy secdep -n sec-ns
template:
metadata:
creationTimestamp: null
labels:
app: secdep
spec:
containers:
- command:
- sh
- -c
- sleep 12h
image: busybox:1.28
imagePullPolicy: IfNotPresent
name: sec-ctx-demo-1
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
- command:
- sh
- -c
- sleep 12h
image: busybox
imagePullPolicy: IfNotPresent
name: sec-ctx-demo-2
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext:
runAsUser: 30000
terminationGracePeriodSeconds: 30
linux@node1:~$ kubectl get deploy secdep -n sec-ns -o yaml | grep -i2 securityContext
|
参考链接:https://kubernetes.io/docs/tasks/configure-pod-container/security-context/
14、TLS安全配置
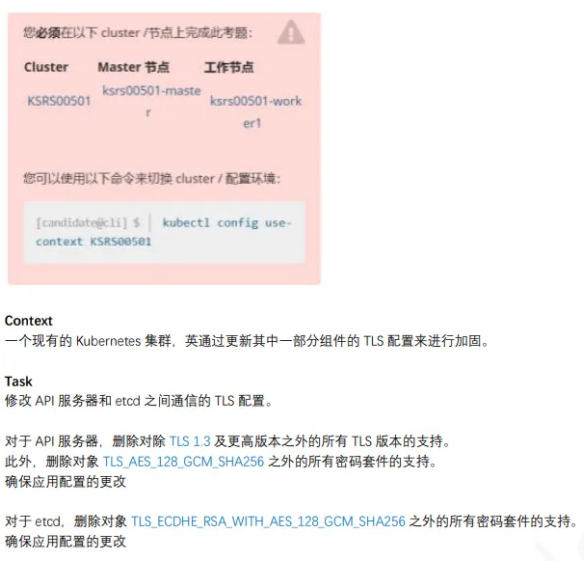
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
linux@node1:~$ kubectl config use-context KSRS
linux@node1:~$ ssh master
linux@master:~$ sudo -i
root@master:~$ cp /etc/kubernetes/manifests/kube-apiserver.yaml /tmp
root@master:~$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
- --tls-cipher-suites=TLS_AES_128_GCM_SHA256
- --tls-min-version=VersionTLS13
root@master:~$ cp /etc/kubernetes/manifests/etcd.yaml /tmp
root@master:~$ vim /etc/kubernetes/manifests/etcd.yaml
- --cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
root@master:~$ systemctl daemon-reload
root@master:~$ systemctl restart kubelet
root@master:~$ kubectl get pod -n kube-system
root@master:~$ exit
linux@master:~$ exit
|
参考链接:https://kubernetes.io/zh-cn/docs/reference/command-line-tools-reference/kube-apiserver/
15、启⽤API server认证
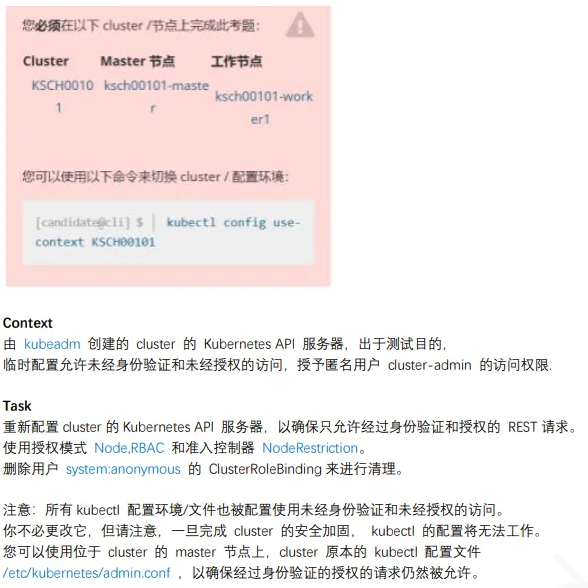
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| root@master:~# kubectl config use-context KSCF
linux@node1:~$ ssh master
linux@master:~$ sudo -i
root@master:~$ cp /etc/kubernetes/manifests/kube-apiserver.yaml /tmp/
root@master:~$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
修改为
- --authorization-mode=Node,RBAC
- --enable-admission-plugins=NodeRestriction
- --anonymous-auth=false
root@master:~$ systemctl daemon-reload
root@master:~$ systemctl restart kubelet
root@master:~$ kubectl get pods -A --kubeconfig=/etc/kubernetes/admin.conf
root@master:~$ kubectl get clusterrolebinding system:anonymous --kubeconfig=/etc/kubernetes/admin.conf
root@master:~$ kubectl delete clusterrolebinding system:anonymous --kubeconfig=/etc/kubernetes/admin.conf
clusterrolebinding.rbac.authorization.k8s.io "system:anonymous" deleted
root@master:~$ kubectl get clusterrolebinding system:anonymous --kubeconfig=/etc/kubernetes/admin.conf
Error from server (NotFound): clusterrolebindings.rbac.authorization.k8s.i
o "system:anonymous" not found
root@master:~$ exit
linux@master:~$ exit
linux@node1:~$
|
参考链接:https://kubernetes.io/zh-cn/docs/reference/command-line-tools-reference/kube-apiserver/
16、ImagePolicyWebhook容器镜像扫描
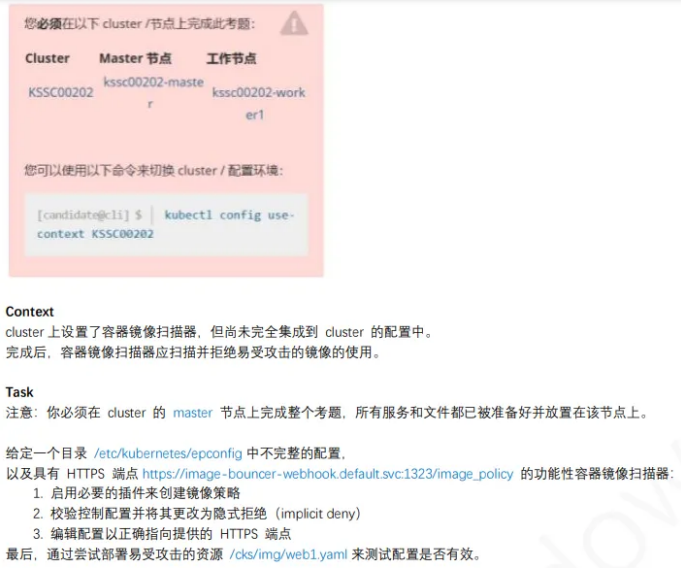
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
linux@node1:~$ kubectl config use-context KSSH
linux@node1:~$ ssh master
linux@master:~$ sudo -i
root@master:~$ vim /etc/kubernetes/epconfig/admission_configuration.json
"denyTTL": 50,
"retryBackoff": 500,
"defaultAllow": false
root@master:~$ vim /etc/kubernetes/epconfig/kubeconfig.yml
certificate-authority: /etc/kubernetes/epconfig/server.crt
server: https://image-bouncer-webhook.default.svc:1323/image_policy
name: bouncer_webhook
root@master01:~$ cp /etc/kubernetes/manifests/kube-apiserver.yaml /tmp
root@master01:~$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
- --enable-admission-plugins=NodeRestriction,ImagePolicyWebhook
- --admission-control-config-file=/etc/kubernetes/epconfig/admission_configuration.json
root@master:~$ systemctl daemon-reload
root@master:~$ systemctl restart kubelet
root@master:~$ kubectl get pod -n kube-system
root@master:~$ kubectl apply -f /cks/img/web1.yaml
不允许创建
|
参考链接:https://kubernetes.io/docs/reference/access-authn-authz/admission-controllers/















